Note: Opinions or statements made in this post are solely my own, and are not the opinions of any organization that I work with or for. Also, I probably got some details wrong... so there's that.
Though I'm not all that concerned about the NSA decrypting my grid certificate, I am interested in how hard it would be. I want to be clear, I am by no stretch of the imagination a security specialist. But I find these kind of discussions interesting. If I say anything incorrect, please leave a comment so I may correct it.
Recent Events
With much of the
recent news that the NSA can decrypt "secure" web traffic, I was curious if they could decrypt my grid traffic, though if they did, it would be quite boring.
Yesterday I read a great
blog post on the possible encryption indications from the perspective of a security researcher,
Matthew Green. In his article, he gave 3 ways to attack the encryption:
- Attack the cryptography. This is difficult and unlikely to work against the standard algorithms we use (though there are exceptions like RC4.) However there are many complex protocols in cryptography, and sometimes they are vulnerable.
- Go after the implementation. Cryptography is almost always implemented in software -- andsoftware is a disaster. Hardware isn't that much better. Unfortunately active software exploits only work if you have a target in mind. If your goal is mass surveillance, you need to build insecurity in from the start. That means working with vendors to add backdoors.
- Access the human side. Why hack someone's computer if you can get them to give you the key?
Will this work on the grid?
Attacking the cryptography
Grid security is based on Public Key Infrastructure (
wikipedia). Each user is issued a Certificate which is then broken into a public key and a private key. Below is a picture of my Mac's keychain view of my certificate:
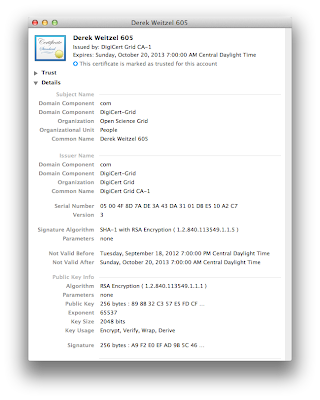 |
| My Certificate |
There are several attributes listed here, but you can see that the key size is 2048 bits. For the RSA algorithm, the largest key publicly factored correctly has been 768 bits (
wiki). It took hundreds of computers months to do so. The NIST and the NSA lists 2048 bit encryption to be the standard for Federal computers until ~2030 (
source), therefore, one can hopefully presume that they provide reasonable security for the time being.
Going after the implementation
Most grid software are use the OpenSSL library to validate certificates. Lets assume that OpenSSL is acceptable (Matthew makes the argument that it may not be), grid software is not known for it's robustness. It is not difficult to imagine that there are unknown security vulnerabilities in the grid software. In the OSG, the 'gatekeeper' software that validates and authorizes users are no less then:
- Globus Gatekeeper (uses various libraries underneath, eventually OpenSSL)
- Bestman
- Gridftp (globus libraries)
- XrootD
- HTCondor
- ...
It may be that not all of these software packages have vulnerabilities, maybe they are all perfect. But it is unlikely, as Matthew says:
software is a disaster.
Further, much of the communication in the Grid is authenticated, but not encrypted. For example, gridftp traffic, by default, is authenticated but not encrypted. Same with XrootD data, authenticated but not encrypted. This data could be easily gathered from anypoint along the network path.
Access the human side
The human side may be the easiest to manipulate. Until recently, the DOE issued all user and host certificates for the OSG. As the DOE is a federal agency, they may be more obligated to work with the NSA than a private company (conspiracy theory hat on). Recently a private company, DigiCert, has issued our certificates.
Of course the NSA could ask the DOE or DigiCert to issue duplicate certificates and could do man-in-the-middle attacks. But as Matthew points out, it seems unlikely that the NSA would be interested in such a direct attack. The unencrypted data could be had so much easier from passive gathering.
But, one has to wonder how many places my proxy is currently living, and how many administrative domains I am trusting, implicitly or explicitly. Just on the top of my head, I know my proxy is at:
- My Laptop
- The HCC GlideinWMS VO frontend
- The 3 OSG GlideinWMS factories
- The 20+ Globus Gatekeepers that we submit to
- Hundreds or possibly thousands of worker nodes across the U.S.
Should we get out our tin foil hats?
Not just yet. It is unlikely that the NSA, or any state entities for that matter, would be interested in the scientific computing resources on a grid. Plenty of garden variety hackers would be interested in the computational power of the grid for bitcoin mining or botnets, but they are unlikely to have the resources to attack any of the above (except possibly the software). The Grid software has been hardened over time to these garden variety hackers, and I am somewhat confident that we can defend against them.
So for the time being, the grid certificates appear to be safe from most threats. Personally, I'm more worried about the software.


Leave a comment